CyberChef


Complex techniques are now as trivial as drag-and-drop. It is read identically to the S-Box matrix. For those comfortable writing code, CyberChef is a quick and efficient way to prototype solutions to a problem which can then be scripted once proven to work. ShiftRows• the first column when multiplied by the matrix, produces the first column of the resultant matrix. No data going to be sent to the server. Other info:• We are going to choose an arbitrary 16 bytes key just for illustrations purposes. At the end, we'll include a note the other variants, and how they differ from the 128-bit version. Each pair of hexadecimal digits requires one byte in binary form, so the value of N depends on the length of the hex string. getPropertyValue b c[b]:void 0,""! Block Encryption Mode SSL Libraries that Support Mode Initialization Vector Required ECB OpenSSL, yaSSL No CBC OpenSSL, yaSSL Yes CFB1 OpenSSL Yes CFB8 OpenSSL Yes CFB128 OpenSSL Yes OFB OpenSSL Yes As of MySQL 5. References [1] [2] [3] [4] [5] A slight modification to that code for Python 3. It also influences password hashing performed by and statements that specify a password using an IDENTIFIED BY clause. It is quite irritating that your sample and the first select-statement I've posted also not work meanwhile, returning the same error as posted above. If crypt is not available on your system as is the case with Windows , always returns NULL. " button depending on whether you want the input message to be encrypted or decrypted. Here's how it works on a clean Pg 9. As input, this method receives the plain text string and encrypts it with the provided key and configurations used in the new function call. querySelectorAll "[selected]". For example, the S-Box transformation of 35 or 0x23 can be found in the cell at the intersection of the row labeled 20 and the column labeled 03. Also, as you're using client-side encryption Browser encryption , it's safe, it doesn't send any data to our servers. Consequently, statements that use this function are unsafe for statement-based replication and cannot be stored in the query cache. Bytes of the internal state are placed in the matrix across rows from left to right and down columns. Hence, you must always use an IV of 128 bits 16 bytes with AES. MixColumns• Nowadays AES is being accepted as one of the most popular and secure algorithms for data encryption and decryption. The three possible key lengths supported by AES allow users to pick a tradeoff between speed and security. The easiest way to install it is using , a Python package manager. Consequently, is also deprecated. Symmetric ciphers use the same or very similar from the algorithmic point of view keys for both encryption and decryption of a message. Unlike standard matrix multiplication, MixColumns performs matrix multiplication as per Galois Field 2 8. Asking for help, clarification, or responding to other answers. The last inverse operation to define is MixColumns. The first operation to be undone is ShiftRows. Please be sure to answer the question. Symmetric ciphers can operate either in the or in the. Wallet credits are not reset on a daily basis, but they are only spent when a user has not enough Daily Credits. YOU CAN NOT Ask anywhere to get the password you made - even to us! CBC mode is highly recommended and it requires IV to make each message unique. It is not the same type of encryption as used for Unix passwords; for that, use. This is a nonbinary string unless the character set is binary. N is 16 for an value and 20 for a value. You can turn off the feature by clicking on 'OFF' or by changing current type of input under the Input text field. When a symmetric cipher mode requires an IV, the length of the IV must be equal to the block size of the cipher. Nonempty strings are stored as a 4-byte length of the uncompressed string low byte first , followed by the compressed string. The flip side is that you have to use to program with aes. It was submitted as an entry to the National Institute of Standards and Technology's NIST competition to select an Advanced Encryption Standard AES to replace Data Encryption Standard DES. Finally, the leftmost byte is exclusive-ored with a round constant. attachEvent "onreadystatechange",K ,a. The key schedule is different for each variant. This means that its inputs are quoted to be evaluated in the context of the data. Like MixColumns, Inverse MixColumns can be defined as the matrix multiplication in Galois Field 2 8. encode "hex" Now that we have our cipher text, we will decrypt it back to plain text. WRITE DOWN Your password and save it on your side! In terms of security, ECB is generally a bad choice since identical plain text blocks are encrypted to identical cipher text blocks [2], which allows a possible attacker to disclose patterns in our ciphered messages. Nobody without the key can read encrypted text, except you and the people you share with and the quantum computers that can unlock your content. AES ciphertexts are decrypted by following the order of operations explained at the beginning of this section, using the appropriate inverse operations and using round keys in reverse order. ECB: Electronic CodeBook• In the case of words 1-3, the value used in the exclusive-or is the previous word words 0-2 of the previous round key. However, see the note regarding the MD5 and SHA-1 algorithms at the beginning this section. How else could I retreive aes-encrypted values? A visual representation of the MixColumns operation is shown above. It's not more than I shown, and I didn't define new functions, its a new installed postgresql. Various tools:• 17, statements that use or are unsafe for statement-based replication and cannot be stored in the query cache. Besides Daily Credits, all accounts, including IP address accounts of anonymous users, have their credit Wallet. Symmetric-key algorithm• In AES, the initial key is used in the initial round of AES as input to the AddRoundKey operation. If it's auth, let someone else do it for you Even better, don't store the password at all, authenticate against LDAP, SASL, Active Directory, an OAuth or OpenID provider, or some other external system that's already designed and working. The S-Box operation used in the AES key schedule is identical to the one used in the encryption phase as described previously. For this to work, the user must have the privilege. S2: select decrypt pw, 'key', 'aes' from demo;• As shown, the operation consists of three stages: an S-Box transformation, a permutation, and an exclusive-or. This encrypt method call will return as output a string with the cipher text. is a symmetric encryption algorithm. Even if you are an anonymous user, you are given some credits to spend. However, use of nonbinary string data types such as or to store compressed strings is not recommended anyway because character set conversion may occur. All IP address accounts are created with an initial Wallet balance of 3. Storing the string also results in slower comparisons because of the larger values and the need to take character set collation rules into account. Finally, we can check the the decryption result, obtained from using the same key. I'll pay for restoring lost password Sorry, we really cannot help with it. Symmetric ciphers are thus convenient for usage by a single entity that knows the secret key used for the encryption and required for the decryption of its private data — for example file system encryption algorithms are based on symmetric ciphers. Callbacks "once memory" ,"rejected"],["notify","progress",n. See the notes at the beginning of this section about storing hash values efficiently. Inverse Initial Round• Rijndael is a family of block ciphers developed by Belgian cryptographers Vincent Rijmen and Joen Daemen. The key-extraction algorithm and the format of the output AES-encrypted message is compatible with OpenSSL. This is illustrated in the Figure below. This function requires MySQL to have been compiled with a compression library such as zlib. compareDocumentPosition;return d? AES-128 : 40 steps• 3 If its a Key, what is the value of IV128? In no event shall the copyright owner or contributors be liable for any direct, indirect, incidental, special, exemplary, or consequential damages including, but not limited to, procurement of substitute goods or services; loss of use, data, or profits; or business interruption however caused and on any theory of liability, whether in contract, strict liability, or tort including negligence or otherwise arising in any way out of the use of this software, even if advised of the possibility of such damage. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. Depending on the selected function the Initialization vector IV field is shown or hidden. Then, we can check the cipher text resulting from encrypting the input plain text. For encryption modes that require an initialization vector, the same vector must be used for encryption and decryption. Any insight from either you or Mark Percival is greatly appreciated. 1 implementation of PASSWORD Calculate and return a password string introduced 5. AddRoundKey• Since it is defined as the standard used by the US government, it is supported by most vendors. The overall structure of the encryption stage of AES is identical for all three variants, but the number of rounds varies for the 128, 192, and 256-bit variants 10, 12, and 14 rounds respectively. Remember that the length of the message to encrypt needs to be a multiple of the block size, which is 16 bytes. If you still need to use , a salt value must be used with it to reduce risk. Thanks for contributing an answer to Database Administrators Stack Exchange! Author: Rajendra Varma Note - Since none of the user information does get stored on server, it is safe to use these tools. This function decrypts data using the official AES Advanced Encryption Standard algorithm. Select the same encryption type as you entered for encryption. Just drag your file over the input box and drop it. Encrypts str using the Unix crypt system call and returns a binary string. To Decrypt your data, follow these steps: 1. This is why we call them Daily Credits. The strength of the encryption depends on the length of key used for encryption. A random salt is injected along with the password to strengthen the encryption code. This function is the SQL interface to the algorithm used by the server to encrypt MySQL passwords for storage in the mysql. If the output is larger than a certain threshold default 1MiB , it will be presented to you as a file available for download. 509 certificate to find out who issued it. Simple functions can be combined to build up a "recipe", potentially resulting in complex analysis, which can be shared with other users and used with their input. As AES is symmetric encryption, this means that the same key is used for encryption as well as decryption of the data. For more information, see the description of. Decrypts a string encrypted with. Calculates an MD5 128-bit checksum for the string. We don't have your password or your data. To undo AddRoundKey, it is only necessary to expand the entire AES key schedule identically to encryption and then use the appropriate key in the exclusive-or. There is a separate worksheet to store the long and unsightly lookup tables such as the S-box. Microsoft Office Open XML Workbook: Preferred format for Microsoft Excel 2007 and above. If an error occurs, returns NULL. To install it via pip, simply send the following command on the command line depending on how you have installed Python and pip, you may need to be in a specific folder such as the Scripts folder before running pip commands : pip install pycrypto This tutorial was tested on Python 2. As of that version, statements that use are unsafe for statement-based replication and cannot be stored in the query cache. AES decryption has also the same process. This should allow new users to try most of Online Domain Tools services without registration. VALUES UNHEX MD5 'abcdef' ,. DO NOT Lose Your Password when encrypt the content! If you have other questions, please contact us. You can check a very illustrative example of the security problems that may arise from using ECB mode. You might need to add explicit type casts. 17 Return a random byte vector Calculate an SHA-1 160-bit checksum Calculate an SHA-2 checksum Uncompress a string compressed Return the length of a string before compression Determine strength of password Many encryption and compression functions return strings for which the result might contain arbitrary byte values. push ":enabled",":disabled" ,a. removeEventListener "DOMContentLoaded",K ,a. It's now on the server's storage, along with the encrypted data. S1: BEGIN;• The result is a binary string of the same length as str. so both the encrypt and decrypt functions expect the key to be bytea. A block cipher AES uses block of 128 bit to divid data to cypher• AES stands for Advanced Encryption Standard and it is a cryptographic symmetric cipher algorithm that can be used to both encrypt and decrypt information [1]. The code The first thing we are going to do is importing the AES module from the pycrypto library. Encryption with AES The encryption phase of AES can be broken into three phases: the initial round, the main rounds, and the final round. As we increase the length of encryption key, the time and complexity of cracking an encrypted data increases exponentially. One way to make collisions detectable is to make the hash column a primary key. AddRoundKey Of the four operations in AES encryption, only the AddRoundKey operation is its own inverse since it is an exclusive-or. The output of the key schedule function is used as the round key input to the AddRoundKey operation in AES encryption. Aim It is hoped that by releasing CyberChef through , contributions can be added which can be rolled out into future versions of the tool. The stream ciphers hold and change their internal state by design and usually do not support explicit input vector values on their input. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. To avoid exposing these, applications can use stored procedures to encrypt and decrypt values on the server side. For , N ranges from 28 to 32 depending on the argument specifying the desired bit length of the result. and lots more. In this operation, the input to the round is exclusive-ored with the round key. AES uses a single S-Box for all bytes in all rounds. However, it works fine here on Pg 9. If either argument is NULL or the hash length is not one of the permitted values, the return value is NULL. It could encrypt your message using strong encryption algorithms, so it will be more secure to send or store, than in plain text. The input can be Base64 encoded or Hex encoded image and. An identical transformation on the round key is performed to produce the next round key. Note Passwords that use the pre-4. Even if you are an anonymous user, you are given some credits to spend. Using the radio buttons under the Key input field, you can specify whether the entered key value should be interpreted as a plain text or a hexadecimal value. Calculates the SHA-2 family of hash functions SHA-224, SHA-256, SHA-384, and SHA-512. If the intended output is a plain-text then, it can be decoded to plain-text in-place. Maybe you have 10 timestamps that you want to parse or 16 encoded strings that all have the same key. The first thing we can see is that the output of the encrypt method is indeed a string. Somewhere something went wrong. To avoid these types of exposure, applications can encrypt sensitive values on the client side before sending them to the server. For use in that context, len must be at least 16. The return string is a binary string where the first character is. The table below possible combinations for key sizes: Key Size Combinations 1-bit 2 2-bits 4 4-bits 16 8-bits 256 16-bits 65536 32-bits 4200000000 56-bits DES 7. For account upgrade instructions, see. We're unable to decrypt it if you lost your password. The latter function is not affected by the value of. What 'Browser encryption' means? S1: LOCK TABLE demo;• However, note that the specific values in both matrices are chosen in a way such that one multiplication is the inverse of the other in Galois Field 2 8. SubBytes The SubBytes phase of AES involves splitting the input into bytes and passing each through a Substitution Box or S-Box. AES-128 and RSA encryption both are not quantum-safe, while In a post-quantum world, AES-256 is still comfortably secure. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. The key length is a trade off between performance and security. length;while e-- delete d[b[e]];if c? OpenPGP: OpenPGP• 2 Input text has an autodetect feature at your disposal. The algorithm first extracts a 128-bit secret key and AES IV initial vector from the password and then after padding the input encrypts it by 128-bit blocks. character is added to avoid problems with endspace trimming should the result be stored in a or column. Enter the same encryption key to decrypt your data. If you want to store these results, use a column with a or binary string data type. ShiftRows In the ShiftRows phase of AES, each row of the 128-bit internal state of the cipher is shifted. The AES S-Box is shown in the Table below. Symmetric ciphers are basic blocks of many cryptography systems and are often used with other cryptography mechanisms that compensate their shortcomings. Cryptographic function Key lengths Initialization vector lengths all modes In bytes In bits In bytes In bits AES 16, 24 or 32 128, 192 or 256 16 128 DES 1 to 8 bytes 8 to 64 16 128 TRIPLEDES 1 to 24 8 to 192 16 128 BLOWFISH 1 to 56 8 to 448 16 128 BLOWFISH-compat 1 to 56 8 to 448 16 128 RIJNDAEL-256 1 to 32 8 to 256 64 512 R4 1 to 256 8 to 2048 - - SERPENT 1 to 32 8 to 256 32 256 TWOFISH 1 to 32 8 to 256 32 256 Table 1. Anyone who will get access to the encrypted message, will be unable to read original message without knowing your password. It can be reproduced without the LOCK TABLE by an unprivileged attacker, it's just harder to time it right. Overall structure of encryption and decryption in Advanced Encryption Standard The four sub-operations of AES are AddRoundKey, SubBytes, ShiftRows, and MixColumns. The 128 is added to make it easier to recognize an encrypted key. Returns a hashed password string calculated from the cleartext password str. Consequently, statements that use this function are not safe for statement-based replication and cannot be stored in the query cache. The initialization vector is added to the file name for convenience. AES algorithm is the successor Data Encryption Standard DES , first published in 1977. AES encryption require a specfic length key to encrypt or decrypt the data. The first key is the default key that is used if you do not specify any key argument to. What is Exactly of AES Encryption Online? The key parameter corresponds to the encryption key to be used by the algorithm and we will pass it the key we previously defined [4]. This function will return an object of class [4], which provides the functions to both encrypt and decrypt the data. See a tidy evaluation tutorial such as the to learn more about these techniques. setAttribute "className","t" ,c. Cipher import AES Next we need to set our secret encryption key. Name Description Decrypt using AES Encrypt using AES Return result as a binary string Decode a string encrypted using ENCODE Decrypt a string Encrypt a string Encode a string Encrypt a string Calculate MD5 checksum deprecated Return the value of the pre-4. Open two sessions, and:• promise ;var L;for L in n l break;l. In the stream mode, every digit usually one bit of the input message is encrypted separately. The key mathematical functions I used are VLOOKUP, BITXOR, DEC2HEX, and HEX2DEC.。 。 。
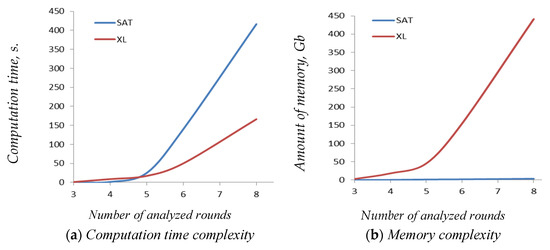
4